Is your information secure? Is your IP protected? Is your Application Specific Integrated Circuit (ASIC) safe from counterfeiters?
Exposing information, stealing IP and full-scale counterfeiting are some of the motives around an ASIC tampering attack. ASIC tampering refers to intentionally changing the functionality of a device or working to uncover proprietary secrets in the design or operation of the ASIC. The increase in counterfeiting of integrated circuit (ICs) is threatening the operation, safety and security of many electronic systems.
Behind the Scenes
Not long ago, I was called into the office of one of our system architects. Our Defense and Aerospace group at onsemi wanted to enhance our current portfolio, which includes ITAR and trusted development with an anti-tamper offering.
I was thrilled. The system architect had already developed an algorithm in Matlab to build an anti-tamper mesh network in a completely unique, random and unrepeatable fashion. I just had to figure out a way to convert the output to a format my layout tools could read, or I could use his basic idea, develop the algorithm in another code and then convert that output for my layout tools. Easy enough, or so I thought.
After about an hour of going over the meeting notes, I realized I was in over my head. I actually had two completely different choices in front of me: I could flounder for months or I could tell management that I wasn’t the right person for the job. Both options seemed like a career-limiting move, but really, I wasn’t the right person. I suggested they pull in my colleague John Davis.
I’ve worked with John for almost 20 years. He was a wrestler in high school and one day during an ill-fated takedown drill, John landed on the mat with such force that he developed tinnitus (ringing in his ears). The condition has become more severe with time, and a few years ago John got hearing aids to help with the condition. When the doctor’s office and staff couldn’t solve the programing and configuration issues, John ordered the software himself. He programmed his own hearing aids and continues to troubleshoot and configure them himself – “because it was just easier.”
In only a couple months, while managing two to three other critical customer projects at the same time, John developed code in various tools to design, simulate, build, instantiate and test what is now the company’s anti-tamper active shield.
Anti-Tamper Elements
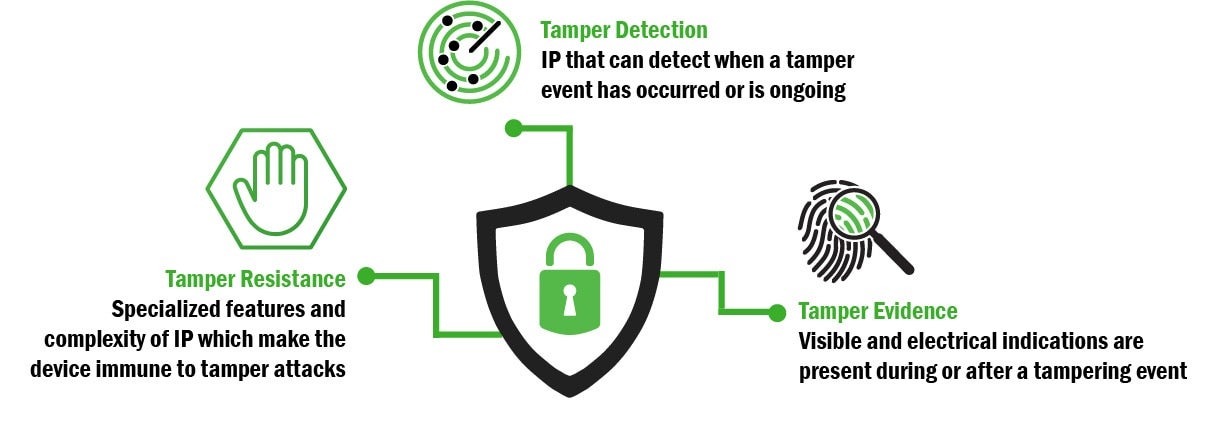
onsemi’s anti-tamper active shield focuses on three aspects of anti-tampering protection. The complexity of the mesh network provides tamper resistance and makes an ASIC more immune to tamper attacks. The specialized features of the mesh network provide tamper detection when a tamper attack has occurred or is ongoing, and when a mesh network is incorporated into an ASIC, visible and electrical tamper evidence are present during or after a tampering event.
Attack Methods Addressed
onsemi’s anti-tamper active shield addresses two specific ASIC tampering attack methods.
An attacker will be unable to easily microprobe the chip’s surface to directly observe, manipulate or interfere with the internal workings of the IC and any attempt to reverse engineer an ASIC or portions of an ASIC are complicated due to the presence of the active mesh network.
How It Works
The mesh network is a continuous, randomly-generated wire segment of top-level metal. One or multiple lines can be applied over desired IP or sensitive areas of the die and each functions as a powered and active shield rather than mere blockage.
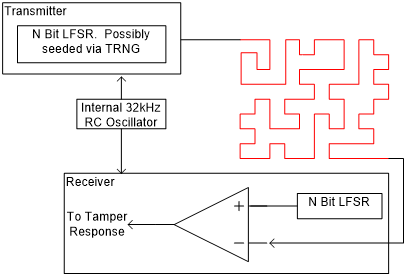
Fig.1 Anti-tamper Mesh Schematic
As shown in Figure 1, a relatively basic state machine is connected to the mesh. A transmitter is at one end while a receiver is attached to the other. The transmitter will send out a pseudo-random sequence, and the receiver will compare the sequence upon receipt. If the mesh network is compromised, the receiver will detect an incorrect sequence and signal a tamper event. The initial data can be hardwired to a fixed value, supplied from a true random number generator (TRNG), or applied from another source.
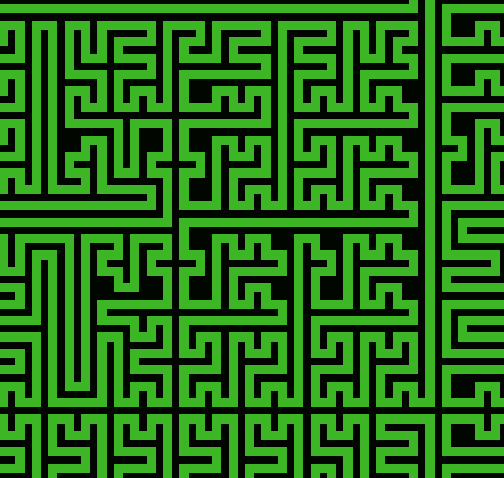
Fig. 2 Example of Mesh Network
The complexity of the onsemi mesh network resides in building the comprehensive, unique route in an automated manner. An example of how a mesh might look when drawn in metal is shown in Figure 2.
Top-level metal is typically the thickest and most often used for power routing, so tradeoffs of mesh size and power grid requirements are analyzed to determine optimal sizes and placements of mesh architectures.
Mesh operation is verified through test and simulation throughout the ASIC development.
Past, present and future
Aerospace and defense applications have long called for anti-tamper strategies, but the accelerated use of personal electronics and IoT devices is compelling other markets to examine anti-tampering capabilities today. To learn more, download the Anti-tamper Active Shield white paper.
For inquiries about onsemi’s anti-tamper active shield, contact: Matt Shreve, Global Product Market Manager Digital, Aerospace and Defense at onsemi.